Thursday, September 30, 2010
Dell's New 7-Inch Tablet
The tablet will compete with Apple’s iPad, the BlackBerry PlayBook, and Samsung’s Galaxy Tab. The new 7-inch will use Google’s Android operating system, but future releases may use Windows. Little pricing information is available for the new product, as well as some of its competitors. If similar to the highly popular iPad, prices could range from approximately $500-$850. The Galaxy Tab, however is priced over $1,000.
To read more about Dell's upcoming release, visit TechnoLog.
Wednesday, September 29, 2010
Are You In Need of An IT Makeover?
Do you have an IT horror story to tell? Could you use a brand new IT setup? CMIT has teamed up with Dell and Microsoft to give one small business (5 or more employees) a $75,000 makeover! We want to hear about your IT horror stories so we can help others prevent future disasters. The winning makeover includes:
- Dell computers, server, and peripherals
- Microsoft Windows 7 Operating System
- Microsoft Office 2010 Software
- CMIT Solutions desktop maintenance, security, and backup services
This contest is open until November 12! We look forward to hearing your IT horror stories and maybe your business will be the winner of the $75,000 Technology Makeover!
Enter your company for a chance to win by visiting our website!www.cmitsolutions.com/techmakeover
Are You Protecting Your Internet Privacy With Firefox Add-Ons?
Monday, September 27, 2010
CMIT @ the Merrick Fair!





Thursday, September 23, 2010
Be Alert for An IRS E-Mail Hoax
 If the message is replied to or you are redirected to another page, malware can infect your computer. Instead, any e-mails that look suspicious should be forwarded to the IRS at phishing@irs.gov.
If the message is replied to or you are redirected to another page, malware can infect your computer. Instead, any e-mails that look suspicious should be forwarded to the IRS at phishing@irs.gov. Wednesday, September 22, 2010
Are You Thinking Of Buying A New Computer?
- Is the computer for the casual user or the business traveler? This can depend if you buy a standard desktop or a high-octane laptop.
- Regardless of who is using the computer, a warranty for a minimum of 3 years should be purchased.
- The Professional Edition of Windows is recommended to best meet the compatibility of files sent from other users.
- Chain retailers are not the best place to purchase a new computer. Instead, reach out to a company that works intensively with computers, such as CMIT.
Since CMIT is a Dell Certified Partner, we are well-informed on all of their equipment and can help you through each part of your next computer purchase.
Read more tips by clicking here:
Tuesday, September 21, 2010
Microsoft Issues Announcement about ASP.net Bug
Microsoft has issued a warning about a web bug that is affecting ASP.net. ASP is a Microsoft application that is used to create websites. This security alert and the details of the attack methods were announced at the Ekoparty Security Conference on September 17, 2010.
The bug allows hackers to view and retrieve files that are on the ASP framework. They can also obtain full administrator rights to any type of activity. Additionally, through the analysis of error messages, hackers can figure out encryption keys and therefore decode all of the cipher text.
Microsoft is currently working on the problem, but recommends that users make some changes to their account in order to block hackers from correctly interpreting error messages. Users of ASP.Net should enable the “CustomErrors” feature and also change their configuration so that every error page is identical (despite various problems). Most of the bug is based on hackers distinguishing error pages, so this will prevent them from doing so. For now, until a patch is released, this is the best preventative measure against this bug.
To read the full article on this bug, visit:
Wednesday, September 15, 2010
Keeping Inventory On Your Technology
 There are five necessary steps to a successful IT Asset Inventory:
There are five necessary steps to a successful IT Asset Inventory: - Record crucial information about all equipment. This includes the make, model, serial number, and date of purchase.
- Gather software installation disks, product keys, and warrantees.
- Keep a record of usernames and passwords.
- Separate data according to the level of importance.
- It is also recommended that all of these documents and paperwork are stored somewhere offsite as well.
If your business needs help completing inventory, CMIT Solutions is here to help!
To read other tips, visit our home office blog:
Tuesday, September 14, 2010
E-Mail Verification Hoaxes
Usually the e-mail claims that the provider is closing unused accounts due to congestion, and that the only way to keep your account active is to reply with the desired information. Some services also claim that they only have a certain amount of user-names left, so they need to close all the inactive accounts. This is an example of an e-mail that is being sent out:
Furthermore, here are the top ways to determine if the e-mail is faulty:
- The e-mail requires you to send your information through a reply e-mail or provides a link that takes you to a spoof page, where your data is then captured.
- The “reply-to” e-mail address or the links look reputable, but when moused over, a different and suspicious address or website is shown.
- The content may appear to be genuine, including logos and links, but one or more of the links may lead to the fraudulent website.
- They include generic greetings such as "Dear Account Holder". The e-mail would usually include the user's name if it were from the actual provider.
- It is common for these e-mails to return at a later date, even if you have already handed over your information. They can even return a day or two later, but not always from the same sender.
If you receive this e-mail, be sure not to give away any of your information. Be careful and use these tips in order to protect your account!
Visit these links to learn more about phishing scams and see examples:
http://www.hoax-slayer.com/phisher-scams.html#phishing-exampleshttp://www.millersmiles.co.uk/identitytheft/021605-Msn-Warning-Message-Your-account-is-near-to-be-disconnected.php
http://www.hoax-slayer.com/yahoo-mail-phish.shtml
http://www.somalia24.com/?p=29559
Friday, September 10, 2010
Apple's 27-inch iMac

The design of the iMac is sleek and clean, it has an "elegant aluminum-and-black-bordered glass look". It is equipped with USB ports, firewire, audio, and ethernet ports all in the back of the screen. On the right side of the screen there is a slot load drive and SD card reader as well. Not only is the size of the screen astonishing, but so is the crisp display. What makes it look so clear is the "high resolution, vibrant colors and pixel-per-inch count".
Take a Look Behind the Screen...
Apple has raised the bar with this all-in-one iMac. The internal composition of the computer holds high value in the world of technology. With the intellegence of Apple's technology team, they have found a way to fit the best hardware and processors built into this computer while maintaining its sleek look.
Read the Full Article about the 27inch iMac here: Computerworld
Wednesday, September 8, 2010
Cloud Computing and the Future
The cloud computing services of Microsoft and Google have been increasingly more popular. Earlier this summer, Microsoft had announced they would provide free, Internet versions of Office programs such as Word, Excel, and PowerPoint. The immediate comparison was drawn to Google Apps, which offers word-processing and spreadsheet creation as well. However, Microsoft deems that these particular versions are not a replacement for the regular Office Suite. Instead, they are intended to be used as an additional resource that could be used cooperatively.
For relatively low prices, businesses can purchase enhanced versions of these programs. For instance, Microsoft offers its Business Productivity Online Standard Suite for $10 a month, while Google Apps merely costs $50 a year. Many smaller businesses have been hesitant to invest time and money into these cloud computing programs. While these services are the newest options available, many prefer to stick with what they know.
In the future, businesses will likely allow for a combination of technology services, including offline and online programs. In a truly collaborative environment, these services will be blended together to create the most efficient and budget-friendly result.
To stay up-to-date with the latest tips and information, visit:
CMIT Home Office Blog
Tuesday, September 7, 2010
Facebook Introduces Enhanced Logout Security
Not only will this feature allow users to eliminate hackers from sending out spam to Facebook friends, but also permit them to Logout from recently used machines. If you have entered your Facebook account from a public computer, for instance, you can remove that computer from the list of approved devices.
This new security feature will gradually be implemented for all Facebook users. They will be able to see a list of computers used, the time and date of logging in, and an estimate of where the account has been most recently been accessed. Users can select to turn on/off the feature of receiving login notifications. They can choose to be notified by SMS or e-mail if another computer or mobile device has logged into your account. This feature was introduced last May, but now with the additional ability to view the list of used machines. Within seconds, it is now easier to protect your account and allow for more enhanced security.
Here are the few easy steps it takes to implement this new security feature:
Once you are logged in, go to 'Account' at the top right corner. Select 'Account Settings'. Then click on 'Account Security' which will bring you to this page --
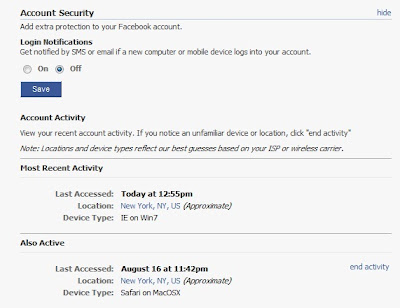 Listed under your account activity there are devices and locations in which your account has been logged into. If any of the devices or locations are unfamiliar to you, you can end activity to secure your account. To make sure you are the only one logging into your account, check the activity every now and then in order to protect others from entering your Facebook.
Listed under your account activity there are devices and locations in which your account has been logged into. If any of the devices or locations are unfamiliar to you, you can end activity to secure your account. To make sure you are the only one logging into your account, check the activity every now and then in order to protect others from entering your Facebook.To read the full article, visit Computer World.
Thursday, September 2, 2010
Hurricane Earl is on its way -- Are You Prepared?
Hurricane Earl is threatening the east coast and it looks like we may get hit hard with this powerful storm. Latest projections show Earl coming within miles of Long Island and the NY Metro area on Friday evening into Saturday morning.
Because of the threat we thought it would be prudent to provide you with some steps to take before and after the hurricane.
PREPARE YOUR TECHNOLOGY:
Be sure you have a full backup of all your important data.
(both on and off-site preferably)
If you have a UPS battery (Uninterruptible Power Supplies with surge protection) be sure the unit is connected and the auto shutdown software is installed and working.
If you do not have a UPS battery on each device we recommend shutting down your PC's and servers if you expect, or are prone to power outages. A sudden loss of power will damage computer equipment. At the very least, be sure you have surge protectors if you do not have UPS units.
We advise you to unplug your PC if you do not have a proper UPS or surge protector.
If you're in a flood prone area, make sure to keep all your computers and hardware off the floors.
PREPARE YOUR HOME & OFFICE:
Enable remote access if you will need to access data from home. (and if you have the aforementioned UPS units in place.)
Take in or secure all outdoor property (furniture, gas grills, sheds, outside storage tanks)
Ensure proper working condition for emergency equipment, such as flashlights and battery powered radio and first aid kids
Clear loose and clogged rain gutters and downspouts
Stock Non Perishable Food, First Aid Supplies and Drinking Water
Make a plan for you and your family pets if you need to evacuate
Have an out of state friend as a family contact, so that all your family members have a single point of contact
Check your battery backups on sump pumps, alarm systems, etc
Move all contents to higher floors if it looks like flooding is imminent (especially items of high or unusual value and vital records)
***If disaster strikes your business during Hurricane Earl and you are forced to relocate, please call us immediately so that we can implement your disaster recovery plan***
Contact us with any questions or concerns about your technology needs.


