Tuesday, August 31, 2010
How Do You Calculate the Cost of Inconvenience?
Remember, time is money.
The higher the salary of the person who’s losing the time, the more money you’re losing. And the more time a high-dollar person spends on minor computer annoyances, the less time they’re spending on adding value to the business.
That’s one of the biggest problems associated with small-business executives wasting even 10 minutes trying to reinstall a mouse driver or retrieve a deleted file. Those are 10 minutes they might have spent following up with a sales prospect or uncovering a major miscalculation in next year’s budget.
Read about our simple formula for determining the true cost of lost time by clicking here:
CMIT Solutions Home Office Blog.
Friday, August 27, 2010
Malware Spread Through USB Devices
A security company reports that a USB drive was used to compromise U.S. military networks in 2008.

Other devices that connect to PCs via USB, including smartphones, cameras and music players, also are a threat, added Corrons. "All these devices have memory cards or internal memories and therefore it is very easy for your cell phone, say, to be carrying a virus without your knowledge."
The USB infection vector isn't new. Two years ago, the 'Conficker worm' made headlines worldwide after it spread using flash drives, among other avenues.
Read this FULL article on Computerworld for more details.
Wednesday, August 25, 2010
Microsoft Release of IE 9 Public Beta
A photo of the new IE9 interface leaked as shown here:
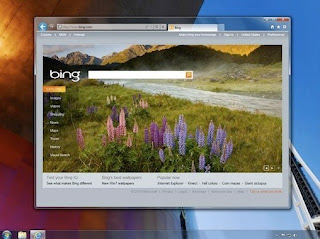
The new browser will run only on Vista and Windows 7, not the much more popular Windows
Microsoft declined to confirm the details leaked by its Russian press site or comment on its IE9 interface plans.
To read more about Microsoft's new release, click the link below.
Reclaim Lost Hours by Making Outlook Sort Your Mail for You
Let’s take a very simple and straightforward example. You’re subscribed to receive daily emails from an airline. These emails are occasionally useful, so you don’t want to drop off the subscription list, but you also don’t want them cluttering your inbox.
Solution: Create a rule that says whenever an email comes in from this particular sender, it goes into its own special folder. That way you can just check the folder whenever it’s convenient for you.
First, create a folder in your inbox called Airline Alerts.
Next, go to the Tools menu and click Rules and Alerts. On the Email Rules tab, click New Rule.
That will bring you to the Rules Wizard, where you have a number of different options. You can use a templated rule, or you can write your own. In this case, we’ll use a templated one because it’s pretty straightforward. The rule we’re going to create will apply to a particular sender upon the arrival of the email. So first, we’ll select the first option: “Move messages from someone to a folder.” Then click the Next button.
The process that follows will ask you a few questions about what conditions the rules should apply under, what action you want the rules to follow, and if there are any exceptions to the rule.
In the next screen, click the first box, which says “from people or distribution list.” This tells Outlook to only apply the rule to messages that arrive from specific people or a distribution list. In the window at the bottom, you’ll see the rule written out in sentence form, with highlighted text indicating where you need to supply a few details. Click on the highlighted text (“people or distribution list” and “specified”) to add your specifications. Here, we’ll use info@AnywhereAirlines.com and the Airline Alerts folder.
The next screen you see will ask you what you want to do with the messages. We just want them to move to the Airline Alerts folder – we don’t want them forwarded, deleted, copied, or anything else – so we’ll click the top box. Then click Next.
You’re now looking at a screen that’s asking you if there are any exceptions to your rule. Are there any conditions under which you wouldn’t want an email from info@AnywhereAirlines.com to go straight into the Airline Alerts folder?
Let’s say you definitely want that email delivered directly to your inbox if the airline has cheap fares to Acapulco, Phoenix, or Reykjavik. Click “except if the subject or body contains specific words,” then go down to the window at the bottom and click that highlighted text. In the next screen, type in those three city names. They’ll automatically appear in the Search List. When you’re done, click OK
Your Rule Description now includes the exceptions you just entered.
In the next screen, you’ll be asked to give the rule a name. It’s best to go with something descriptive that will remind you about what the rule involves.
Click Finish, Apply, and OK. You’re done!
For a more detailed description of this process that includes images to walk you through it, click here: CMIT Solutions Home Office Blog.
Wednesday, August 18, 2010
"One Note": The Best Project Management and Note Taking Tool
Second, OneNote carved out an early following among tablet PC users and maintains a bit of its niche reputation, even though it’s well suited to laptop or desktop use. (Its handwriting recognition features make it a natural fit for the tablet PC and for anybody who relies heavily on handwritten notes -- such as students, mathematicians, and engineers.)
OneNote basically takes a number of different input types -- typed text, handwritten text, images, and more -- and collects them all in a single easy-to-navigate interface. It's basically set up like a notebook, with tabs to separate sections, and a second tier to define pages within each of those sections.
Read more by clicking here: One Note Support Page
Tuesday, August 10, 2010
How You Can Use The Web To Become A Better Leader
That’s where the web comes in. Online learning is exploding, and webinars are one of the most effective ways you can develop your skills without investing a lot of time or money. McLeod, who runs a sales and leadership training firm, says, “Personal development doesn’t have to be boring, expensive or time-consuming. We do a lot of webinars for our clients because it enables us to take a single topic, like selling skills, employee engagement or organization skills, and provide people with quick, easy to use advice and tools, no travel required.”
CMIT has partnered with McLeod to create a webinar series titled “Grow Your Small Business Without Giving Up Your Life.” As a CMIT QuickTip subscriber, you’re invited to attend for free. (registration info below)
Here are McLeod’s 10 Tips for getting the most out of any webinar:
1. Be Choosy - Your time is valuable. Look for webinars that provide true skill development rather than just an overview of something. Think about what would have the biggest impact on your life or business.
2. Consider the Source - Look at who’s offering the webinar and who’s leading it. There are tons of webinars out there and many of them are just sales pitches in disguise. Make sure the webinar is sponsored by a trusted source and is being delivered by an expert in the field.
3. Expect Takeaways - A good webinar should provide you with a downloadable tool you can use right away and that you can share with your employees and colleagues.
4. Block Out Time – Treat the webinar as you would a client meeting or any other important appointment. If you’re serious about your development, you'll schedule time for it.
5. Turn Off Email – Multi-tasking is a myth. If you’re going to attend, make sure you’re fully focused.
6. Log On Early – Many webinar providers, including CMIT's provider Go To Meeting, do a system check and take a minute to load, especially the first time. Log in a few minutes early to make sure you’re ready before the official start time.
7. Choose Your Audio – Webinars usually give you the option of dialing in via phone, or listening via your computer. Make your choice when you log in. If you want to be able to ask questions and your computer doesn't have a microphone, choose the phone option. If you choose listening from your computer, make sure your speakers and mic are on.
8. Participate - If the webinar gives you an option; by all means participate. It will make the call more meaningful for you and everyone else. In many cases, if you ask a question you’ll get expert advice from someone you might not otherwise have access to.
9. Share Recordings – Most webinars provide a link to a recording of the call after the fact. If you learned something, share it with your colleagues and employees.
10. Apply and Enjoy – The ideal webinar is entertaining AND informative. So take a breath before you start, grab pen and paper to record useful info, settle into your chair, and show up with a learner attitude. This is about improving your business and your life, it should be fun and interesting.
CMIT Solutions Home Office Blog.
Friday, August 6, 2010
Secure Search Gives You Extra Privacy on Google
First, the “why.” The most common reason for wanting to do an encrypted search is the same reason you’d want any Internet transmission to be encrypted: it inhibits snooping by third parties.
But there are other reasons, as well. In an unencrypted Google search, the search term is saved in your search history and will autopopulate the next time you type in the beginning letters of the phrase. With encrypted search, those terms aren’t stored locally so they won’t pop up.
As PCWorld’s Tony Bradley points out business confidentiality can be seriously threatened by unencrypted search. Read by clicking here: http://www.pcworld.com/businesscenter/article/196949/benefits_of_google_encrypted_search.html
[Unencrypted] searches may yield hints regarding ongoing research and development, confidential intellectual property, upcoming product or service announcements, or other sensitive information that is not intended for unauthorized consumption. Google encrypted search does not store that information, so there is no risk of someone stumbling onto it later.
Bottom line: if you’re doing confidential research on the Web, you should definitely consider doing it over an encrypted connection.
Read more on the CMIT Solutions Home Office Blog.
